VPNs allow you to create a secure, encrypted connection from your device to a remote server. The server will then connect back from the remote device through the internet, creating a private tunnel. Site-To-Site VPNs are used to bridge networks that must be connected together because of a lack of direct connectivity. For example, many companies use site-to-site VPNs as an alternative to public Wi-Fi or as a way for employees in different countries or networks to work together online.
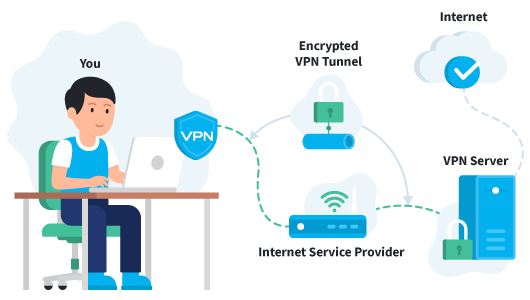
(Image Source: VPNoverview)
While this technology is incredibly useful and often necessary, there are also some drawbacks and risks associated with using it. Here’s a full breakdown of what these features are and how they work.
What Is a Site-To-Site VPN?
A site-to-site VPN allows a business to create a secure connection between different sites, which can be between two different buildings, cities or countries. For example, let’s say you’re an American business that wants to expand its operations into Japan. Using a site-to-site VPN connection, you would be able to securely connect your American offices with your Japanese operations office using encryption and authentication protocols.
Site-to-site VPNs can also be used in private offices with remote workers. For example, let’s say you have a small business with an office in New York that employs three people. You could use a site-to-site VPN to connect your office to an employee who works remotely out of their house. This would allow for private, secure access to the internet (assuming you hire someone tech-savvy enough to set up the VPN).
How Does A Site-To-Site VPN Work?
Like the local network on your home computer or laptop, each site that participates in a site-to-site VPN requires its own router that is connected to the central server (usually located at another company’s office). The connection between these two routers is made via encryption and authentication protocols. While it’s not possible to discuss these protocols in much detail, we will discuss the main components.
Before starting the VPN connection, you need to set up your devices with specific settings to allow VPN traffic. Any device that needs to be connected via a site-to-site VPN must have an external IP address. This means that no matter which computer or device you are using, you’ll always be able to connect via this method. Every device connected through a site-to-site VPN must have an external IP address configured individually. This is done for two reasons:
Security – You will not be able to access sites that are not included in the connection.
Traffic Limitations – A separate external IP address is needed for each device that is connected to the VPN. This means that if your site-to-site VPN has five computers with employees working at different times, you will need five external IP addresses assigned.
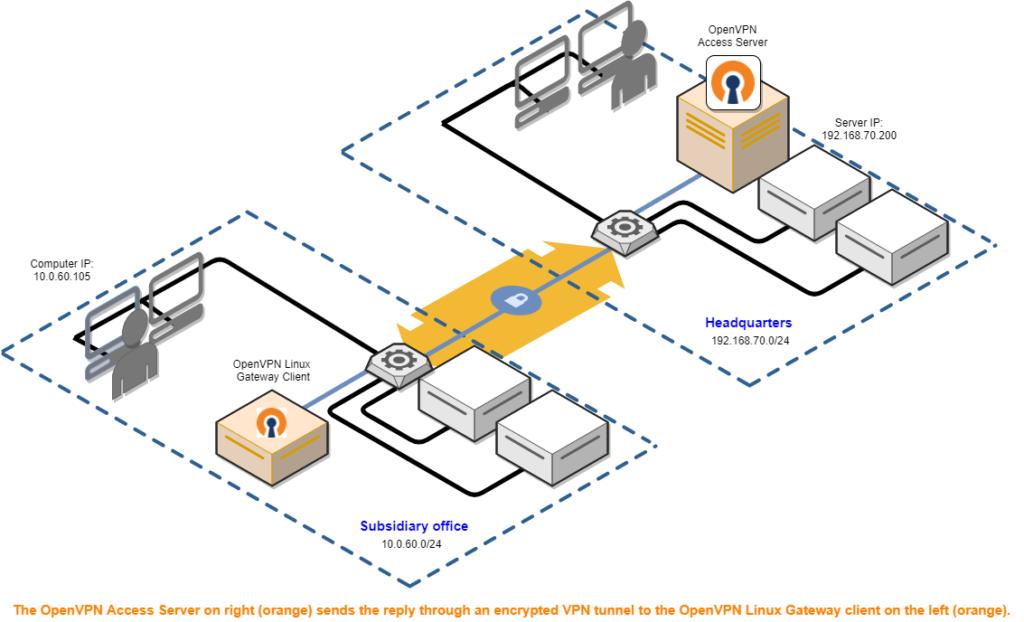
(Site-to-site VPN demonstration: Open VPN)
Once each device has an external IP address, you are now able to start your site-to-site VPN connection. Depending on the type of service you want and how many computers you’re connecting to, you can set up this connection with either an internet provider or a third-party provider. For the most part, you will have to use a third party service. Without this service, your site-to-site VPN connection would be limited to your internal network.
When you sign up for a suitable VPN provider, you will usually have access to their software so that it’s easy for you to create your site-to-site VPN connection. The software that comes with the service is very user friendly and usually has an easy to understand set of instructions on how to connect. You can use the software at home on your personal computer (when connected via Wi-Fi), or you can use it when connecting multiple devices together in different places.
Once you’ve successfully connected and started your site-to-site VPN, all the computers and devices will need to use the same internal IP address (supplied by the service) to communicate with each other. If one computer is not using this IP address, it will not be able to connect or access anything on your internal network. The IP address chosen needs to be static and not change over time (this is why companies like Google recommend using Dynamic DNS for each device).
Downside of site-to-site
While using a site-to-site connection is secure and can be useful for any type of business, there are some downsides and risks. The biggest drawback is that you can’t use this connection to access the internet like you would normally. You will only be able to link your internal sites and networks together, and nothing beyond those two locations. This could be a problem for businesses who want to create a site-to-site VPN for employees who work remotely because they won’t be able to easily access anything on the outside (assuming the remote workers are using their own external IP addresses).
Another drawback is that site-to-site VPN connections are more expensive than using your internet provider. While nearby offices may qualify for lower pricing, companies that plan on networking across multiple states or countries should expect to pay more. Moreover, you won’t have access to the full benefits of a VPN connection. For example, if you use a cloud-based VPN connection, you can track usage and data transfers. However, with a site-to-site VPN connection, the only information that will be logged is your IP address, which isn’t much use to anyone.
Site-to-Site Vs Cloud Based VPNs
In addition to working with your internet provider and third-party service providers, there are also two other possible ways that you can obtain a site-to-site VPN: through a cloud-based service.
Cloud-based VPNs are virtual networks that are housed in a third party’s server. Using this “cloud” server allows you to connect your business computers to the internet without worrying about setting up your own equipment. Cloud-based VPNs can be useful if you have limited space at work. With cloud-based VPNs, you can access the internet via Wi-Fi or other wireless networks without having to worry about adding more devices to your office.
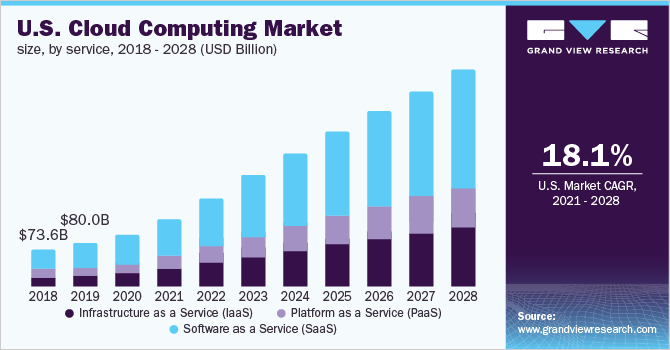
(Image Source: Grand View Research)
While cloud-based VPNs are great for some companies, they are not always preferable for others. For example, there is a risk associated with using cloud-based devices because this gives strangers access to your business’s network and data.
While there is no need for most businesses to use cloud-based VPNs, it’s essential to ensure that you use a trustworthy provider with suitable security protocols in place if you choose to use them.
How To Set Up Your Own Site-To-Site VPN
As mentioned previously, setting up a site-to-site VPN is not difficult. Still, it does require some advanced knowledge about networking and the necessary hardware needed for this type of connection.
Getting started with a site-to-site VPN is as easy as connecting the computer to the internet and then connecting it to your internal network. You can connect to your internal network like you would with a cloud-based VPN: by directly connecting the computer to a Wi-Fi or Ethernet that is not connected to the internet.
Your main concern here will be that you don’t have any devices on your internal network that are connected via a VPN already because you don’t want to confuse any existing connections. So to prevent data from being corrupted by other devices on your network, you’ll have to disconnect all other networking devices from your corporate LAN.
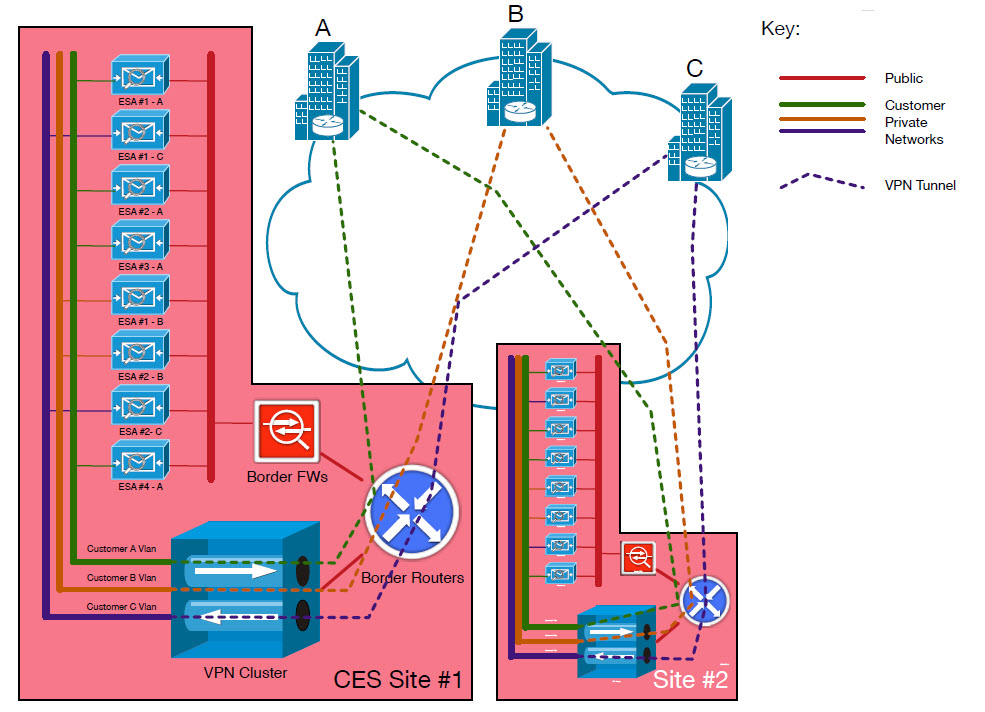
(Image Source: Cisco)
Once you’ve disconnected other networking devices, you can start setting up your site-to-site VPN connection. Initially, your computer will be a part of both LANs. So the first step is to link your computer to your internal network, which means that the IP address on the internal network will have to be different from the IP address on the internet.
To do this, you will need a device that can perform network address translation (NAT), which is usually done by a router or firewall. The router will allow only requests from the VPN computer into your internal network. It will then translate these requests into recommendations that are compatible with the private network and relay them back to you over a secure connection over the internet.
The next step is to allow traffic from your internal network to get out. To do this, you’ll have to set up a second private network that uses the same IP address scheme that you used for the first one. Finally, you will simply have to configure your VPN client with settings that are compatible with both of the networks. Then, everything should be ready for users to connect.